Resilience
- small developer orgs that don’t have time or expertise to deal with common security needs
- large developer orgs that need consistency, scale, and governance of their security capabilities
-
Point north.
-
What time is sunset today?
-
Trace the water you drink from rainfall to your tap.
-
When you flush, where do the solids go? What happens to the waste water?
-
How many feet above sea level are you?
-
What spring wildflower is consistently among the first to bloom here?
-
How far do you have to travel before you reach a different watershed? Can you draw the boundaries of yours?
-
Is the soil under your feet, more clay, sand, rock or silt?
-
Before your tribe lived here, what did the previous inhabitants eat and how did they sustain themselves?
-
Name five native edible plants in your neighborhood and the season(s) they are available.
-
From what direction do storms generally come?
-
Where does your garbage go?
-
How many people live in your watershed?
-
Who uses the paper/plastic you recycle from your neighborhood?
-
Point to where the sun sets on the equinox. How about sunrise on the summer solstice?
-
Where is the nearest earthquake fault? When did it last move?
-
Right here, how deep do you have to drill before you reach water?
-
Which (if any) geological features in your watershed are, or were, especially respected by your community, or considered sacred, now or in the past?
-
How many days is the growing season here (from frost to frost)?
-
Name five birds that live here. Which are migratory and which stay put?
-
What was the total rainfall here last year?
-
Where does the pollution in your air come from?
-
If you live near the ocean, when is high tide today?
-
What primary geological processes or events shaped the land here?
-
Name three wild species that were not found here 500 years ago. Name one exotic species that has appeared in the last 5 years.
-
What minerals are found in the ground here that are (or were) economically valuable?
-
Where does your electric power come from and how is it generated?
-
After the rain runs off your roof, where does it go?
-
Where is the nearest wilderness? When was the last time a fire burned through it?
-
How many days till the moon is full?
-
What species once found here are known to have gone extinct?
-
What other cities or landscape features on the planet share your latitude?
-
What was the dominant land cover plant here 10,000 years ago?
-
Name two places on different continents that have similar sunshine/rainfall/wind and temperature patterns to here.
- Intro - my process and tools
- The Books - which books I recommend
- Analysis - some introspection and goalsetting
- Previously - links to prior years
- Books I plan to re-read
- Deluxe or art-filled editions
- Books I will use as a referenrce
- Books I enjoyed and want to keep around
- The Six Deaths of the Saint (Into Shadow #3) - Alix E. Harrow (see also)
- Nemesis Games (Expanse #5) - James S.A. Corey
- Ursula K. Le Guin: Conversations on Writing - David Naimon
- Lifespan - David A. Sinclair
- The Scout Mindset - Julia Galef (see also)
- Eye of the Needle - Ken Follett
- Where the Deer and the Antelope Play - Nick Offerman (see also)
- Four Thousand Weeks - Oliver Burkeman (see also)
- Gilead - Marilynne Robinson (see also)
- Anthem - Noah Hawley (see also)
- Animal Farm - George Orwell
- The Screwtape Letters - C.S. Lewis
- Great Minds of the Eastern Intellectual Tradition - Grant Hardy
- The Great Mental Models (Vol #1) - Shane Parrish
- The Blade Itself (First Law #1) - Joe Abercrombie
- This Is Your Mind on Plants - Michael Pollan
- Before They Are Hanged (First Law #2) - Joe Abercrombie
- Babylon’s Ashes (Expanse #6) - James S.A. Corey
- Hunting Magic Eels - Richard Beck
- Algorithms to Live By - Brian Christian & Tom Griffiths
- Norse Mythology - Neil Gaman
- Nature Wants Us to Be Fat - Richard J. Johnson
- Rediscipling the White Church - David W. Swanson
- Reaper Man (Discworld #11) - Terry Pratchett
- Late in the Day - Ursula K. LeGuin
- The Future Is Female - Lisa Yaszek
- Into the Odd (Remastered) - Chris McDowall
- How to Take Over the World - Ryan North
- Persepolis Rising (Expanse #7)- James S.A. Corey
- The Arm of the Starfish (O’Keefe #1) - Madeleine L’Engle
- Dread Nation (Dread Nation #1) - Justina Ireland
- Recursion - Blake Crouch
- Meet the Austins (Austins #1) - Madeleine L’Engle
- Undercover (Into Shadow #5) - Tamsyn Muir
- A Load of Hooey - Bob Odenkirk
- The Fat Switch - Richard J. Johnson (superseded by Nature Wants Us to Be Fat above)
- Bury Your Dead (Inspector Gamache #6) - Louise Penny
- Lexicon - Max Berry
- On Juneteenth - Annette Gordon-Reed
- Roadside Picnic - Arkady & Boris Strugatsky
- The Autobiography of Malcolm X - Alex Haley
- All We Can Save - Ayana Elizabeth Johnson & Katharine K. Wilkinson
- Nimona - Noelle Stevenson
- Station Eleven - Emily St. John Mandel
- Ninth House - Leigh Bardugo
- Comedy Comedy Comedy Drama - Bob Odenkirk
- Everything Happens for a Reason - Kate Bowler
- Persephone (Into Shadow #2) - Lev Grossman
- The Little Book of Hygge - Meik Wiking
- Keeper of the Lost Cities (Keeper of the Lost Cities #1)
- Tell the Machine Goodnight
- The Prophet
- A Calling for Charlie Barnes
- The School for Good Mothers
- The Garden (Into Shadow #1)
- Engineer
- Analyst
- Influencer
🔒 Banks: practice internet safety!
Also banks: we won’t let you login if you are blocking junk in your browser or using a VPN
🔒 The opportunity: application threat modeling & secure design review is one of the highest value appsec/prodsec activities, but is hard to implement efficiently and at scale.
A bad solution: provide a long list of controls that need to be checked each time
A better solution: generate relevant security requirements automatically based on what’s being built
Met with primesec yesterday, and this is what they are trying to do! They are using LLM to read what’s in your user stories (etc.), summarizing the work for the security team, and injecting specific security control requirements.
If this catches even a small portion of the real requirements, it would be a major uplift for teams both from a security and efficiency perspective. Looking forward to checking it out.
🔒 Met with the folks from Pangea yesterday.
Looks like it could be an interesting solution for:
🔒 Just left Silicon Valley Bank.
Did not know they still existed!
I’m at AppSec San Francisco this week.
Mute that “🔒” tagmoji if you don’t want to hear about it.
Send me a message if you want to meet up.
📚 The Coddling of the American Mind
Read: The Coddling of the American Mind by Greg Lukianoff and Jonathan Haidt
Recommended
My Reading Highlights and Notes
INTRODUCTION The Search for Wisdom
🔒 OSS backdoors: the folly of the easy fix - lcamtuf’s thing
Even when it comes to lesser threats, the bottom line is that we have untold trillions of dollars riding on top of code developed by hobbyists. The companies profiting from this infrastructure can afford to thoroughly vet and monitor key dependencies on behalf of the community. To be sure, a comprehensive solution would be a difficult and costly undertaking — but it’s not any harder or costlier than large language models or self-driving cars.
🔒 Guest lectured again. Had to be remote because COVID. The professor has a habit of getting a shot when I have a funny line on the slides.
Last time I was doing code/bug examples and my slide said “what could go wrong?”
This one is talking about rules of engagement and responsible disclosure.
🔒 23andMe wants us to accept new terms that change their “Dispute Resolution and Arbitration” process. I wonder what might have spurred that change?
How many of these can you answer about the bioregion where you live?
It seems appropriate that these questions came up (during my daily highlights review) on a colonial holiday. May we re-orient ourselves to deep connection over superficial exploitation.
The Bigger Here Bonus Questions:
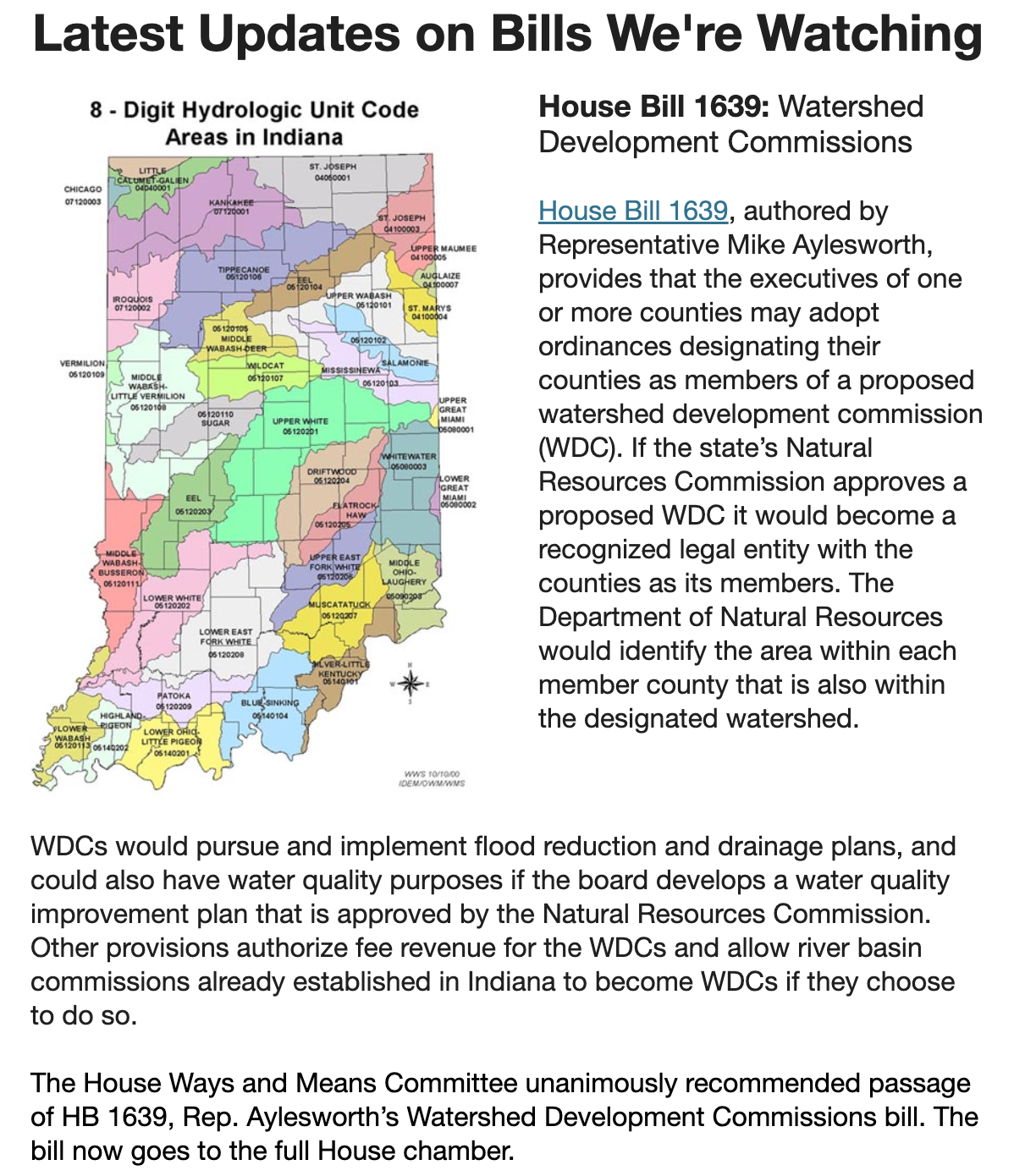
Indiana lawmakers could further dilute state wetlands protections following SCOTUS decision
As our weather gets worse, politicians do, too?
🕊️♻️ Good workshop on Climate Anxiety, Hope, and Resilience this morning. #MennoCon23
Once again I made the call to reorient our conferences and districts to our watersheds.
The White River Alliance is issuing an urgent action request to protect Indiana wetlands. This is important for flood & drought management, ecosystems, biodiversity, and much more.

Positive legislative update courtesy of White River Alliance, regarding HB1639.
📚 2022 Book Review
Welcome to my yearly summary of books!
Table of contents:
Note: I will use Bookshop affiliate links when available, throughout this post. You don’t have to buy from my bookshop, but if you do, I put that money back into more books.
Intro
I use and recommend Libby for getting ebooks and audiobooks from the library. Most books I borrow digitally, but there are exceptions:
For those cases, I get physical editions via Bookshop. And lest you think I don’t really do physical books: my household has 15 brimming bookshelves.
I take copious highlights and notes, and save them to Readwise. Here’s how. Highlights and notes are especially important for me with digital books, where spacial-temporal recollection is not as easy, but spaced-repitition and note-linking can make up for it (and then some).
I track my reading in The StoryGraph. I prefer it because not Amazon and because it incorporates some data elements other than ratings which are useful for describing and finding books. I’m hoping micro.blog’s bookshelves feature continues to improve, so that I could rely on book tracking directly in my blog, as well. (Today, it doesn’t handle book search well nor let us use our own Bookshop links, but we’ll see what the future holds.)
I keep my to-read/wishlist as a Bookshop list, for ease of sharing and gift-giving.
The Books
Let’s start with the recommended ones, collected in this Bookshop collection or visually:

And here are all the books I read, individually, and in reading order (within rating):
⭐️ ⭐️ ⭐️ ⭐️ ⭐️ :
👍:
🤷♂️:
👎 (authors and links removed because I feel bad about even putting these in, but wanted to show the broader view):
Did you read anything I did? What’d you think?
Based on looking at my list, is there anything you’d recommend?
Analysis
This was an mixed year for reading goals. I exceeded by book goal (55 out of 53) but missed by pages goal (15,868 out of 17,500). I’ll go for 60 books next year, but keep the 17,500 page goal.
Similar to my normal ratio, I read 63% fiction this year:
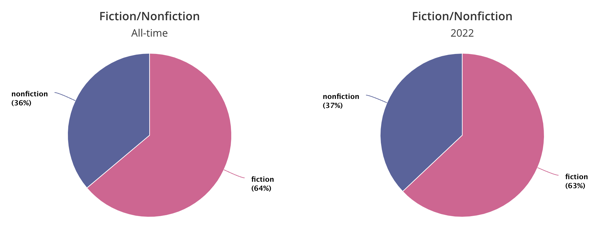
I continue to add to my intentionality in reading, seeking a variety of voices, formats, styles, etc. With such a long list of things I’d like to read, I’m also trying to be wiser about what I should read sooner than later such as things related to health or permaculture.
Here’s to a good year of reading!
Previously 📚:
🔒 A Mental Model for Cybersecurity Operating Modes
A person in risk & security can generally be thought of as acting like one of the following:
Interestingly (and helpfully), this is independent of official title. You’ve probably met engineers whose main operating mode is as the advocate, or leaders who act more like high-level analysts, or ops or risk analysts who focus on building capabilities.
Like all models, this has limitations, but it is useful. It can help you think about what’s missing, where strengths are, what structure should look like, etc.
H/T to David Ames who introduced me to this concept, though with a different name for the third role.
Want to contribute to the White River Report Card?

